Federal Identity, Credential and Access Management F-ICAM
There are 5 parts to Federal Identity, Credential and Access Management System. This is a combination of applications, tools, standards and policies.
Identity Management

Identity Management is how an agency collects, verifies, and manages attributes to establish and maintain enterprise identities for federal government employees, contractors, and authorized mission partners. This service does not apply to public or consumer identity management. The Identity Management services in the Federal ICAM architecture include Creation, Identity Proofing, Provisioning, Maintenance, Identity Aggregation, and Deactivation. These services are sometimes collectively known as Identity Lifecycle Management.
Credential Management

Credential Management is how an agency issues, manages, and revokes credentials bound to enterprise identities. A credential is a data structure that authoritatively binds an authenticator to an existing identity using one or more identifiers. The following are types of authenticators:
- Something you know, like a password or PIN.
- Something you have, like a private key or One-Time Password (OTP) generator.
- Something you are, like a fingerprint or iris.
The Credential Management services in the Federal ICAM architecture include Sponsorship, Registration, Generation & Issuance, Maintenance, and Revocation.
Access Management

Access Management is how an agency authenticates enterprise identities and authorizes appropriate access to protected services. Policy administration is a combination of laws, regulations, rules, and agency policies that secure access to agency services. Your agency determines the requirements for an individual to access each resource category, and they can be as simple or as complex as you need. The Access Management services in the Federal ICAM architecture include Policy Administration, Entitlements Management, Authentication, Authorization, and Privileged Access Management.
Federation
Federation is the technology, policies, standards, and processes that allow an agency to accept digital identities, attributes, and credentials managed by other agencies. The Federation services in the Federal ICAM architecture include Policy Alignment, Authentication Broker, and Attribute Exchange.

Governance
Governance is the set of practices and systems that guides ICAM functions, activities, and outcomes. To perform effective governance, agencies must collect data about ICAM functions from many sources, such as policies and entitlements stores, and analyze this data. Proper data analytics help agencies monitor compliance with established information security policies. The Governance services in the Federal ICAM architecture include Identity Governance, Analytics, and Mitigation.

Homeland Security Presidential Directives
Homeland Security Presidential Directives (HSPDs) appeared soon after the September 11 attacks, and are sometimes issued concurrently as a National security directive.
Protecting and keeping government assets secure such as facilities, computers, or information systems, are a fundamental responsibility of government employees. To ensure consistent implementation across the federal government, Homeland Security Presidential Directive 12 (HSPD-12) was enacted. HSPD-12 provides for a new standardized federal identity credential that is designed to enhance security, reduce identity fraud, and protect the personal privacy of those issued government identification.
FIPS 201 is the technical standard that HSPD-12 required the National Institute of Standards and Technology (NIST) to develop. FIPS 201 is entitled Personal Identity Verification (PIV) for Federal Employees and Contractors. The standard requires the collection of fingerprint and facial information for inclusion on the credential. (Government agencies already use such information to differing degrees depending on the agency.) The PIV credential will contain both a “contact” smart chip and a “contactless” chip. Containing both a “contact” and “contactless” chip will allow the credential to be read by devices that need direct contact with the credential and devices that can read the credential remotely. FIPS 201 was issued on February 27, 2005. The first revision of FIPS 201-1 was finalized in June 2006. The second revision of FIPS 201-2 was finalized in August 2013.
Personal Identity Verification PIV
A Personal Identity Verification (PIV) credential is a US Federal governmentwide credential used to access Federally controlled facilities and information systems at the appropriate security level. PIV credentials have certificates and key pairs, pin numbers, biometrics like fingerprints and pictures, and other unique identifiers. When put together into a PIV credential, it provides the capability to implement multi-factor authentication for networks, applications and buildings.
Enabling systems and facilities to use PIV credentials for authentication enhances agency security. PIV credentials allow for a high level of assurance in the individuals that access your resources, because they are only issued by trusted providers to individuals that have been verified in person. PIV credentials are highly resistant to identity fraud, tampering, counterfeiting, and exploitation. PIV credentials are standardized as well.

Smart Card
PIV cards are known as smart cards. A smart card, chip card, or integrated circuit card (ICC or IC card) is a physical electronic authorization device, used to control access to a resource. It is typically a plastic credit card-sized card with an embedded integrated circuit (IC) chip. Many smart cards include a pattern of metal contacts to electrically connect to the internal chip.
Card readers are needed to read PIV cards. Card readers are available in many shapes and sizes – to fit both the PIV credential, and to plug into your computers. There is a card reader that will work for any shape and size of the computer you use including card readers for USB and microUSB ports. For PIV credentials, middleware refers to the computer software or drivers which allow the computer to interact with the PIV credentials to support authentication, digital signatures, encryption, and integrations with your software tools.
Certificates
Almost all of the methods for using your PIV credential for networks, applications, digital signatures, and encryption involve the certificates and key pairs stored on your PIV credential. There are also scenarios where additional information (such as biometrics) is also accessed and used.
Within the U.S. Federal Government, the certificate and PIV credential information is governed by standards, policies, and implementation-specific choices (options) across all agency credential providers. Typically, there are four certificates and four key pairs on a PIV credential. However, one pair (i.e., one certificate and one key pair) is ALWAYS on every PIV credential and three pairs (i.e., three certificates and three key pairs) are SOMETIMES on a PIV credential. You can review the Basics of a PIV Credential to view the four pairs and purposes.
Identity certificates are issued and digitally signed by a certification authority. The certification authority that signed your PIV certificates is called an intermediate certification authority because it was issued a certificate by another certification authority. This process of issuing and signing continues until there is one certification authority that is called the root certification authority.
The full process of proving identity when issuing the certificates, auditing the certification authorities, and the cryptographic protections of the digital signatures establish the basis of Trust for PIV credentials and certificates.

Network Authentication
The following are required to setup network authentication.
- Users have PIV credentials and PIV card readers
- You are using Microsoft Active Directory to manage your Windows network
- Domain Controllers are Microsoft 2008 R2 or 2012 or above
- User workstations are joined to your network and are Windows 7, Windows 8, or Windows 10-based
Based on this, there are five configuration categories that need to be completed. These include
- Network Ports and Protocols
- Domain Controllers
- Trust Stores
- Account Linking: Associating PIV credentials with User Accounts
- Group Policies and Enforcement
Trust Stores
You want your Active Directory domain, including servers and workstations, to trust user’s PIV credentials for authentication. Trust and certificate chains are reviewed in the Certificate Trust overview, and this page includes information on configuring your Active Directory domain. There are two trust stores to consider for your Active Directory domain:
CAC Cards
In 2001, the DoD first introduced Common Access Cards (CAC), a smart card used to prove identity and log on to systems, with no consolidated and interoperable ID management for civilian employees, reservists, active duty personal and contract workers. In 2006, the DoD launched an updated CAC adding Personal Identification Verification (PIV) capability as a next generation CAC solution. Today, the basic ability for workers and contractors to log into their super-secret systems is the same as it was in the early days of the internet, and the government has not kept up with technology advancements.
The CAC, a “smart” card about the size of a credit card, is the standard identification for active duty uniformed Service personnel, Selected Reserve, DoD civilian employees, and eligible contractor personnel. It is also the principal card used to enable physical access to buildings and controlled spaces, and it provides access to DoD computer network and systems.
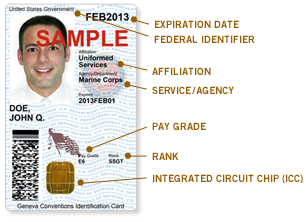
https://en.wikipedia.org/wiki/Common_Access_Card#/media/File:Img-card-topology-front.png
References
USA Identity Management
https://piv.idmanagement.gov/
GSA Access
https://www.fedidcard.gov/faq/1
https://www.energy.gov/hc/services/benefits/new-employee-orientation/security-forms-and-information
eof